Understanding Proxy: The Essential Guide To Internet Privacy And Security
In today's digital age, the concept of a proxy has become increasingly important for individuals and businesses alike. A proxy serves as an intermediary between your device and the internet, allowing users to browse the web more securely and privately. This article will delve deep into the world of proxies, exploring what they are, how they work, and their various applications.
As concerns over online privacy and security continue to rise, understanding proxies can help users navigate the digital landscape with greater confidence. Whether you are an individual looking to enhance your online privacy or a business seeking to safeguard sensitive information, proxies offer a valuable solution. This comprehensive guide aims to provide you with the knowledge necessary to utilize proxies effectively, ensuring a safer and more secure online experience.
Throughout this article, we will cover the different types of proxies, their advantages and disadvantages, and best practices for choosing the right proxy service. By the end of this guide, you will have a thorough understanding of proxies and their role in enhancing internet privacy and security.
- Brittany Force Boyfriend The Love Life Of A Racing Champion
- Puffiddy And Jay Z The Dynamic Duo Of Hiphop
Table of Contents
- What is a Proxy?
- How Proxies Work
- Types of Proxies
- Advantages of Using Proxies
- Disadvantages of Using Proxies
- How to Choose a Proxy Service
- Common Uses of Proxies
- Conclusion
What is a Proxy?
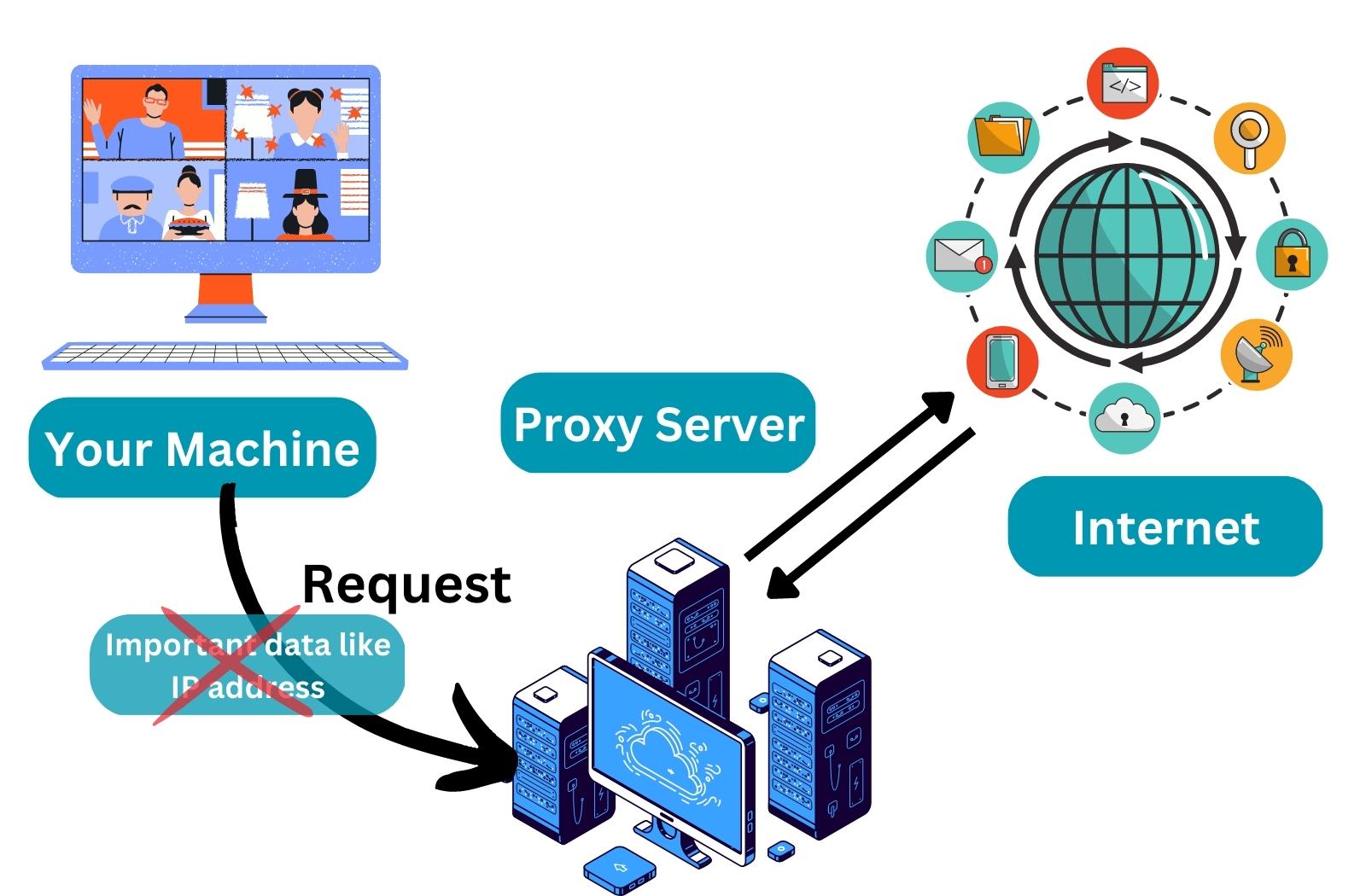
A proxy is a server that acts as an intermediary between a user's device and the internet. When a user requests a resource from the internet, the request is sent to the proxy server, which then forwards the request to the target server. Once the target server responds, the proxy server sends the data back to the user.
Proxies serve various purposes, including enhancing online privacy, bypassing geographical restrictions, and improving internet speed. By masking the user's IP address, proxies provide a layer of anonymity, making it more challenging for third parties to track online activities.
How Proxies Work
Proxies function by intercepting the communication between a user's device and the internet. Here’s a step-by-step breakdown of how proxies work:
- Does Rob Zombie Have Children Discovering The Family Life Of The Rock Icon
- Clint Walker The Iconic Star Of Westerns
- The user sends a request to access a specific website or resource.
- The request is directed to the proxy server instead of the target server.
- The proxy server processes the request and forwards it to the target server.
- The target server responds with the requested data.
- The proxy server receives the data and sends it back to the user.
This process not only allows for better privacy but can also help users access content that may be restricted in their geographical location.
Types of Proxies
There are several types of proxies, each serving different purposes and offering unique features. Below are some of the most common types of proxies:
Forward Proxy
A forward proxy is the most common type of proxy server. It acts on behalf of the client, forwarding requests to the internet. Forward proxies are often used to access blocked content or to hide a user’s IP address.
Reverse Proxy
A reverse proxy, on the other hand, acts on behalf of the server. It receives requests from clients and forwards them to the appropriate backend server. Reverse proxies are commonly used to manage traffic, distribute load, and enhance security for web applications.
SOCKS Proxy
SOCKS (Socket Secure) proxies provide an additional layer of security by routing traffic through a proxy server. They support various protocols and can handle any type of traffic, making them versatile for different applications.
HTTP Proxy
HTTP proxies are specifically designed for handling web traffic. They are often used for caching web pages to improve loading times and can also filter content based on specified criteria.
Advantages of Using Proxies
Using proxies offers several benefits, including:
- Improved Privacy: Proxies mask your IP address, making it harder for websites and advertisers to track your online activities.
- Access to Restricted Content: Proxies allow users to bypass geographical restrictions and access content that may be blocked in their region.
- Enhanced Security: Proxies can provide an additional layer of security, protecting sensitive information from cyber threats.
- Increased Performance: By caching frequently accessed web pages, proxies can improve loading times and reduce bandwidth usage.
Disadvantages of Using Proxies
While proxies offer numerous advantages, they also come with some disadvantages:
- Potential Security Risks: Not all proxies are secure. Some may log user data or expose sensitive information.
- Slower Speeds: Depending on the proxy server’s location and load, users may experience slower internet speeds.
- Limited Encryption: Many proxies do not provide encryption, leaving data vulnerable to interception.
How to Choose a Proxy Service
Choosing the right proxy service is crucial for maximizing the benefits while minimizing risks. Here are some factors to consider:
- Type of Proxy: Determine which type of proxy best suits your needs, whether it’s a forward, reverse, SOCKS, or HTTP proxy.
- Security Features: Look for proxies that offer encryption and do not log user data.
- Performance: Choose a proxy service with a reputation for fast and reliable connections.
- Customer Support: Reliable customer support can help resolve issues quickly and efficiently.
Common Uses of Proxies
Proxies are utilized in various scenarios, including:
- Web Scraping: Proxies are often used in web scraping to avoid IP bans and gather data from multiple sources.
- Anonymizing Browsing: Users employ proxies to browse the internet anonymously and protect their privacy.
- Bypassing Censorship: Proxies allow users to access blocked websites and circumvent government censorship.
- Testing Web Applications: Developers use proxies to test the performance and security of web applications.
Conclusion
In summary, proxies play a vital role in enhancing internet privacy and security. Understanding what proxies are, how they work, and their various types can help users make informed decisions about their online activities. While proxies offer numerous advantages, it is essential to choose a reliable proxy service that prioritizes user security and privacy.
We encourage you to explore the world of proxies and consider how they can benefit your online experience. If you found this article helpful, please leave a comment, share it with others, or check out our other articles for more insights!
Thank you for reading, and we hope to see you back on our site for more informative content!
- Khabibs Wife A Deep Dive Into The Life Of The Mma Champions Partner
- Unveiling The Life Of Adriana Limas First Husband

EP26 Proxy vs reverse proxy by Alex Xu
Guide To Proxy Servers How They Work And Why You Need Them

What Is a Proxy Server Used For? (And How Does It Work?) Kinsta®